Deep into the Systems.
In-depth penetration testing to discover deadly vulnerabilities.

Deep Penetration Testing.
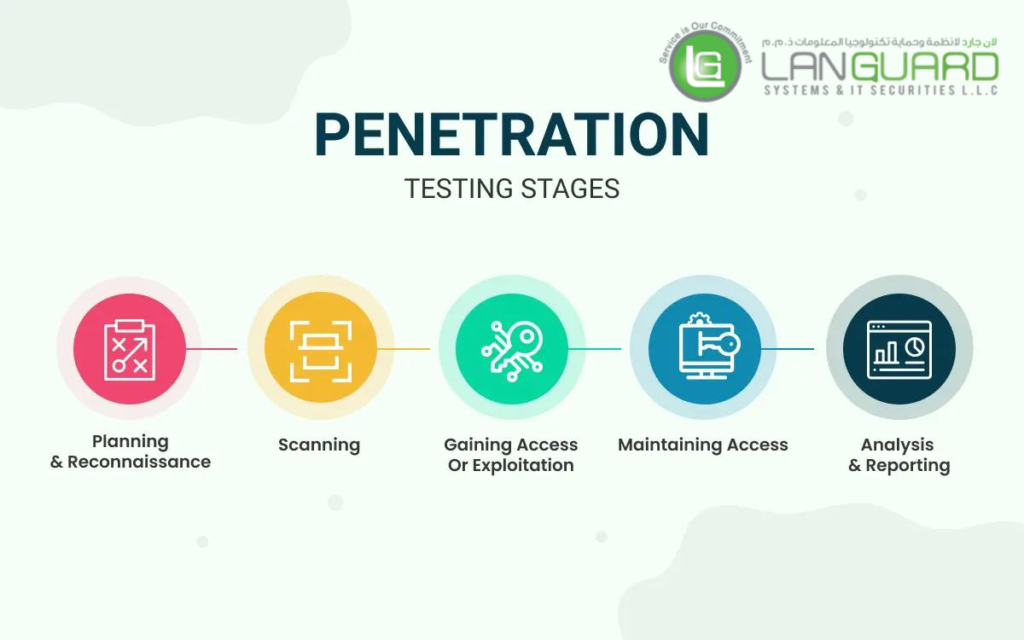
VAPT (Vulnerability Analysis and Penetration Testing) is one among the foremost common cyber security services opted for by quite of our customers round the globe. Penetration testing is the method where we become real hackers and penetrate deep into the systems so as to search out vulnerabilities.
Penetration testing has become one among the foremost elementary needs in cyber security services and it’s extremely counseled to search out loopholes, and strengths of the applications. Our Professional team of hackers have received appreciation from around five hundred brands like Bentley, Mercedes Benz, and Walmart for penetrating into their systems.
That team is currently offered at your disposal to deep check your systems and applications with the foremost effective methods and industry-standard tools.
Depth
Our hackers go in-depth to search out vulnerabilities in your system.
Standards
We use industry-standard tools to search out even the bad loopholes.
Report
Get a penetration testing report that is fully customized for you.
VAPT Services
360° PROTECTION
No extra space for black-hat hackers.
Web Application Security Assessmet
Analyzing all the corners of a web application to make sure safety.
Network Security Assessment
Ensuring safety at network levels while not compromising.
Mobile Application Security
Mobile applications deep testing to avoid loopholes that matter.
IOT Security Testing.
Activating the lights when action needs attention.
Wireless Penetration Testing
Safer wireless networks are nothing however necessary security.
Cloud Application Security Assessment.
Cloud isn't the limit, making certain correct security is that the limit.
WordPress Security Audit & Assessment.
WordPress may not be the foremost secure, however we make it secure.
ERP Security Audit & Assessment
Sensitive business info is even safer with Languard.
SCADA VAPT
Data systems are safer than ever, we ensure 360-degree coverage.
Secure Code review
The code can be written in any style, we have a safe style.
Email Security Audit
Emails reach the correct recipient, the correct means, safe and secure.
Red Teaming
Understand attacks and guarantee 360-degree coverage.
Security Architecture Review.
Architecture desires security, we make sure that.
Device Security Audit & Assessment
The Device is a one-shot game, build it as secure as it gets.
Managed Threat Hunting.
Find threats even before they decide to execute them to the systems.
OT Security Assessments.
360 Degree security assessment by skilled hackers
Purpleteam Assessment.
Red and Blue team, each at work creating it look purple
API Security Assessment.
Communication must be secure, although it's API.
Annual Security Program
Advanced Security Penetration Testing as a Service.
