Services & Solutions For All Industries
The three pillars of cybersecurity
Any cybersecurity strategy is only as strong as its weakest link. That’s why it is fundamental to identify and mitigate risks by applying standards and good practices throughout the whole line of defense which must integrate people, processes, and technology.
People
Strong cyber protection requires an educated and aware workforce. In many cases, your people are your first and last line of defense. A crucial element of this area is creating and communicating a company-wide security culture, advanced by ongoing training.
Processes
In order to identify and eliminate cyber risks, you need to establish and adhere to good processes, practices, and policies. Companies should begin with consistent, regular risk and threat assessments and gap analyses.
Technology
Your cyber defense is only as strong as the technology deployed to manage and control your operations. This aspect is all about protecting what your company develops and deploys, as well as ensuring that the technology coming from your supply chain vendors is secure.
Vulnerability Assessment and Penetration Testing
As a manufacturer itself, Languard embeds security throughout its vendor-neutral, open, IoT-enabled architecture and platform. It includes an open but tailored stack of connected products; edge control level solutions and software; and cloudbased apps, analytics, and services.
End-to-end cybersecurity supports applications and data analytics, embedded across these layers, which converge IT and OT equipment and solutions, software, and services within six domains of expertise.
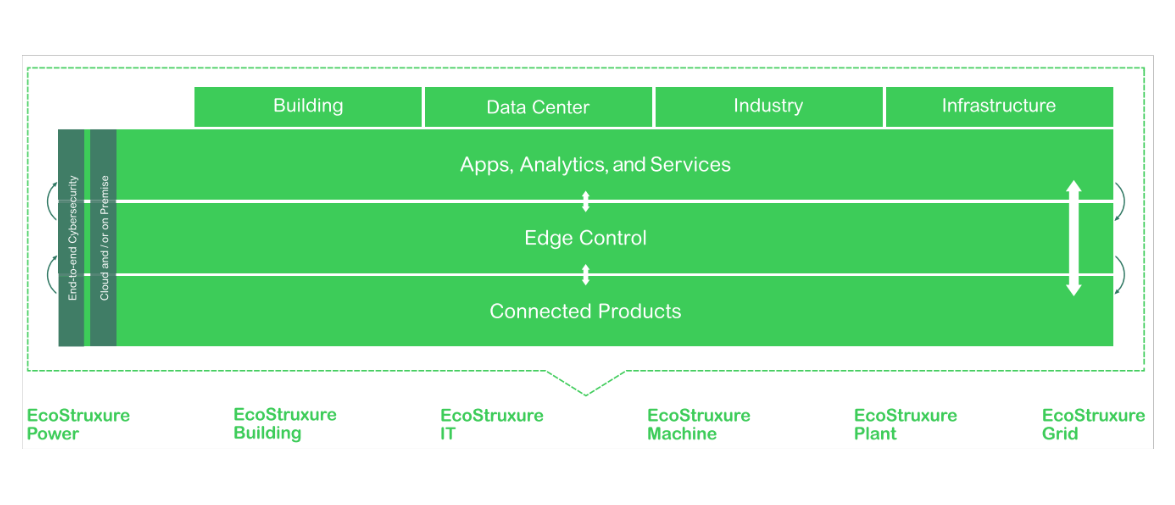
A defense in depth approach
Companies expect that the products they buy include everything necessary to mitigate cybersecurity risks. But the products alone are only a starting point. The way the systems are implemented and integrated into your environment is also critical. The processes for implementation and integration of systems must protect the integrity of your environment. Once the systems are operational, many other aspects must be considered as part of the overall operation, depending on your risk assessment. These range from simple firewalls to network segregation and testing
Addressing cybersecurity challenges on multiple levels
Effective cybersecurity encompasses your entire OT environment – from products and systems through to ongoing services
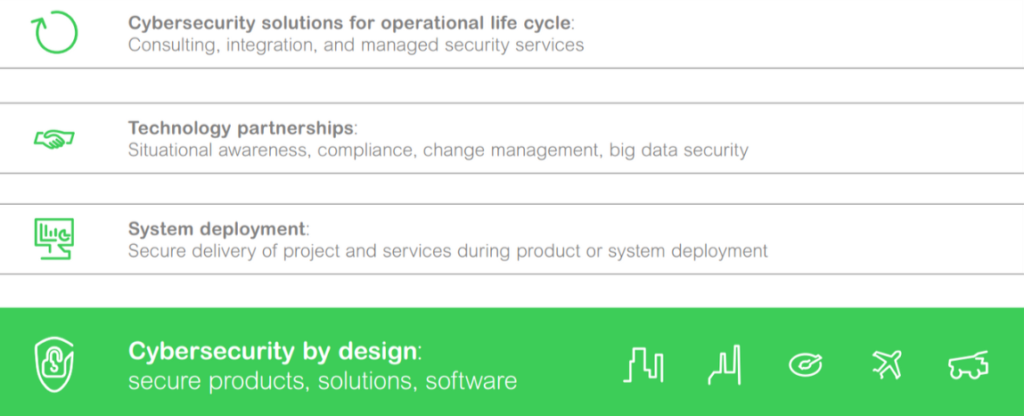
Defense in depth approach
- A certified team of cybersecurity experts who understand your process requirements, enterprise needs, and business environment.
- A dynamic ecosystem of partnerships and platforms including governments, universities, and suppliers that help drive research, policy, and collaborative projects to produce a holistic, security-conscious offering.
- An ISO conformant vulnerability management process that is activated upon external notification, vulnerability disclosure, or customer report.
- An advanced global threat intelligence center that actively monitors cyberspace for threats to our products and customers.
-
150+ products that are cybersecurity standards certified for electrical and process installations
